Mexico to Deport 500 Migrants Who “violently” and “illegally” Tried to Storm United States Border at San Ysidro Port of Entry
MEXICO DEPORTING VIOLENT MIGRANTS …
Reuters is now reporting that Mexico is going to deport approximately 500 migrants who violently tried to storm the San Ysidro port of entry Sunday. This is in response to the illegal and violent actions of the migrants.
If there was ever a reason to build a wall and prevent such lawlessness from occurring, the time is now. No one has a problem with legal immigration, this is not it.
Mexico will deport migrants from a group of 500 who on Sunday tried to “violently” and “illegally” cross the U.S. border, the Mexican Interior Ministry said in a statement.
The statement added that Mexican authorities had contained the protest at the crossing between Tijuana and San Diego and that, despite heightened tensions there, Mexico would not send military forces to control 7,417 migrants from a caravan currently amassed at the U.S.-Mexico border.
Posted November 26, 2018 by Scared Monkeys Build that Wall, Deportation, Illegal Immigration, Mexican Border Security, Open Borders - Border Security, US Border Patrol, US National Security | no comments |
President Trump Threatens to Shut U.S. Border with Mexico Permanently
MAYBE THIS IS WHAT IS NEEDED UNTIL ORDER CAN BE RESTORED …
From the UK Daily Mail, President Donald Trump threatened to permanently close the U.S. border with Mexico on Monday, saying he’ll take the drastic action if members of a swelling migrant caravan are not deported back to their Central American homelands. Following the actions of this weekend where U.S. Border Patrol fired tear gas canisters and rubber bullets at a group of migrants as hundreds tried to storm the border and who also threw ‘projectiles’ that hit border officers. This nonsense must come to an end. Why would anyone want such people in the United States who would act this lawlessly?
At some point the people of the United States need to figure out whether we are a sovereign nation and conduct ourselves under the rule of law or if we are a third word country where anything goes. If we have no borders, then I also assume the assumption is there are no state borders and all property lines and fences mean nothing as well.
‘We will close the border permanently if need be’: Trump threatens decisive action unless Mexican government deports caravan migrants as hundreds storm border and officers fire tear gas and rubber bullets into crowds of people
- President Trump threatens to shut U.S. border with Mexico permanently if migrant caravan is not deported
- He called on Congress to fund his border wall, declaring that the caravan is ‘not coming into the USA’
- Migrants threw ‘projectiles’ that hit U.S. Border Patrol agents on Sunday at the San Ysidro Port of Entry
- Officers responded by firing tear gas and rubber bullets into crowds of people as they neared the border
- Ultimately about 30 made it across, according to a report quoting a Mexican official
- Tensions prompted U.S. officials to close the crossing between Tijuana and San Diego
- Trump’s tweeted ultimatum played on TV screens Monday alongside images of screaming, coughing children
- Homeland Security Secretary Kirstjen Nielsen said she would not put up with the ‘lawlessness’
- Mexico vowed Sunday to deport about 500 who tried to ‘violently’ and ‘illegally’ cross the border
Posted November 26, 2018 by Scared Monkeys Build that Wall, Deportation, Illegal Immigration, Mexican Border Security, Open Borders - Border Security, US Border Patrol, US National Security | one comment |
Accused Capital Gazette Newsroom Shooter’s Stalking Victim Says She Warned Police About Jarrod W. Ramos … “He Will Be Your Next Mass Shooter” … Also Made Threats Against the Capital Gazette
COULD ANOTHER MASS SHOOTING HAVE BEEN PREVENTED?
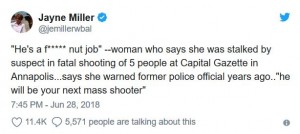
As reported at the UK Daily Mail, the gunman, Jarrod W. Ramos, who murdered five people at the Capital Gazette newspaper in Annapolis, Maryland was known to police, had a vendetta against the newspaper with a previous defamation law suit, had made threats against the newspaper and was exposed in the past for his perverted campaign of harassment. The women who was the victim of Jarrod Ramos’ harassment and stalking told police that he would be “the next mass shooter.” The unidentified women told WBAL reporter Jayne Miller that she had become so frightened of Ramos that she had to move three times and now sleeps with a gun, and added, he is a “f*cking nut job”.
I guess we can now say, that was an understatement as this predatory lunatic with a vendetta murdered 5 members of the Capital Gazette newspaper on Thursday. This sicko was flagged as “the next shooter” by an individual who had been unmercifully harassed to police and guess what … Jarrod Ramos became maybe not the next, but one of the next mass shooters. The question is was Jarrod W. Ramos legally allowed to own a gun after having plead guilty to criminal harassment? Should more have been done? Because of this man’s history and threats, should his home have been checked? We hear that Annapolis, MD is a close fit community, where law enforcement and the local news paper were always in contact. Previously, individuals from the news paper feared Ramos would do something ad they didn’t feel safe.
The gunman who murdered five people at a newspaper in Annapolis, Maryland, had been flagged up to police as ‘the next mass shooter’ by a woman he obsessively stalked – and had a vendetta against the publication because they exposed his perverted campaign of harassment.
Jarrod W. Ramos’ harassment of the woman, one of his former high school classmates, had been the subject of a 2011 article in the Capital Gazette, which would later see him sue the newspaper.
After the unsuccessful lawsuit, and years of posting threats against the newspaper and its staff on social media, the 38-year-old opened fire in their newsroom on Thursday afternoon, killing five and injuring two.
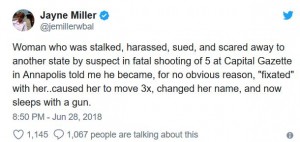
Ramos’ initial stalking of his former classmate had begun with a Facebook message of thanks for being ‘the only person ever to say hello or be nice to him in school’, and escalated into a harassment campaign which saw her forced to change her name and leave the state.
The woman told a WBAL TV reporter that she had become so frightened of Ramos that she had to move three times and now sleeps with a gun, adding that he is a ‘f***ing nut job’.
The beginning of Ramos’ vendetta against the Capital Gazette. Ramos had a long time feud with the newspaper. In 2012, Ramos filed a defamation lawsuit against the paper and a columnist over a July 2011 article that covered a criminal harassment charge against him. After his lawsuit was dismissed by the Courts because he failed to prove what the newspaper printed was untrue. As we have always stated, its hard to defame one’s character, when one has no character. Thus, a mental case became even more of a mental case, complete with threat after threat against the paper. His twitter account is reported to have regularly commented on Anne Arundel County news and referred to a deadly shooting at the French newspaper Charlie Hebdo in 2015. The account had been dormant since January 2016 and then at 2:37 p.m. Thursday, just moments before the Capital Gazette shooting, the account posted a message that read: “F— you, leave me alone.”
The 2011 Capital Gazette article about Ramos harassment of the woman was headlined ‘Jarrod wants to be your friend’, and was published after he pleaded guilty to criminal harassment.
The article, quoted in its entirety in the 2013 defamation lawsuit, described how Ramos had sent the woman numerous emails spanning several months, calling her vulgar names and telling her to kill herself.
The Capital reported that he also contacted the woman’s job; she was suspended by a supervisor the same month and then let go several months later, which she believes was due to Ramos.
‘When she blocked him from seeing her Facebook page, he found things she wrote on other people’s pages and taunted her with it, attaching screenshots of the postings to some of his emails.
‘She called police, and for months he stopped. But then he started again, nastier than ever.
‘All this without having seen her in person since high school.’
In the years that followed the publication of the article, Ramos sued the newspaper, the reporter who initially wrote about the case, a judge and the woman who testified against him.
His defamation suit was thrown out on appeal in 2015 because Ramos failed to prove that what the newspaper had printed was untrue.
Ramos would go on to routinely harass journalists from the Capital Gazette on Twitter in scores of profanity laced posts.
One of Ramos’ tweets targeted one of the journalists killed on Thursday, Rob Hiaasen.
In another tweet, he discussed how he’d enjoy seeing the paper stop publishing, but ‘it would be nicer’ to see two journalists ‘cease breathing’.
Other tweets from his account referenced previous journalist shootings, including the 2015 terror attack on the Charlie Hebdo offices in Paris.
Sadly, we cannot 100% individuals who are hell-bent on murder. The Arundel County police and other first responders should be applauded for their immediate response to the crime scene. They saved lives. However, even with a 60 second response by law enforcement, five people were murdered. This means three things. One, people need to be able to arm and defend themselves. Two, because of the treats, businesses should have better security. Three, law enforcement needs to be more proactive with lunatics like this.
Posted June 29, 2018 by Scared Monkeys Death Threats, Law Enforcement, Media, Murder, Newspapers - print media | no comments |
Shooting at Capital Gazette Newspaper in Annapolis, Multiple People Shot (Update: Shooter in Custody)(Update: 5 Confirmed Casualties)
BREAKING … SHOOTING AT CAPITAL GAZETTE NEWSPAPER!
According to reports, there has been a shooting at the Capital Gazette in Anne Arundel County, Maryland. Reports from the Baltimore Sun is that a gunman shot through the glass door to the office and opened fire on multiple employees.
A shooting has occurred at the Capital Gazette in Anne Arundel County, a paper that is owned by The Baltimore Sun, according to reports from Gazette staff.
Anne Arundel County Police confirmed there was an “active shooter” at 888 Bestgate Road, where the newspaper’s offices are located. The Bureau of Alcohol, Tobacco, Firearms and Explosives confirmed it was responding to a “shooting incident” at the Gazette.
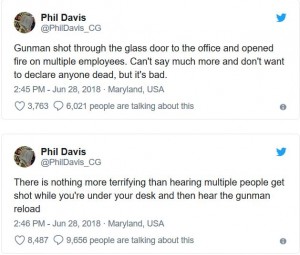
Phil Davis, a Gazette crime reporter who was there at the time of the shooting, said that multiple people had been shot. Police did not immediately respond to requests for further information.
“Gunman shot through the glass door to the office and opened fire on multiple employees. Can’t say much more and don’t want to declare anyone dead, but it’s bad,” Davis wrote on Twitter as he waited to be interviewed by police. “There is nothing more terrifying than hearing multiple people get shot while you’re under your desk and then hear the gunman reload.”
Police said the building was being evacuated as officers continue searching it.
UPDATE I: Tweets from Phil Davis, the crime reporter of the Capital Gazette Newspaper as the shooting was taking place.
Shooting at Capital Gazette newspaper in Annapolis, Md.
UPDATE II: CBS Baltimore is reporting that 4 Deaths Reported After Shooting At Capital-Gazette Building In Annapolis.
According to police, first shots were reported at 2:40 p.m. after the shooter entered the Capital-Gazette building.
Police say the building has been evacuated, and officers are continuing to search the building.
UPDATE III: Suspect reported in custody. The suspect was reported to be a white male. A law enforcement official tells CNN that one person is in custody, believed to be a shooter at the Gazette building. The source said there are multiple wounded.
BREAK!NING NEW TONIGHT 6/28/18 PRESS BRIEFING ON MARYLAND SHOOTING
UPDATE IV: President Trump, as well as the first lady, have been briefed on the shooting, White House officials confirmed. White House Deputy Press Secretary Lindsay Walters said “our thoughts and prayers are with all that are affected.”
Maryland Gov. Larry Hogan tweeted that he was “absolutely devastated to learn of this tragedy in Annapolis.”
UPDATE V: From 4:38 Police Presser:
- Several people have died, several others injured.
- Shooter is in custody and being interviewed by police
- Officers got on scene with 60 to 90 seconds of call.
- Gov. Larry Hogan praised first responders and police
- The investigation has just started, there will not be many details.
- Many witnesses being interviewed.
- The building is secure, we feel there are no other shooters in the building. However, its being considered a crime scene.
- 5 fatalities confirmed.
UPDATE VI: CBS News reporting that suspect refusing to identify himself.
One law enforcement source says the suspect is a white male in his 20s and didn’t have identification in him. The suspect is refusing to identify himself.
UPDATE VII: 5:30 Presser:
- 60 seconds to respond to crime scene.
- Building is tactically secure, no more persons in building a threat to anyone else.
- They found what they think was one explosive devise.
- 170 people evacuated from building.
- Gun used described as a long gun
- There was no gun fire exchanged between suspect and officers.
- Another update will be at 8pm ET.
- 3 people estimated injured in hospital.
UPDATE VIII: Bizarre, Annapolis shooting suspect damaged his finger tips to thwart identification.
The suspect accused of killing five people in a shooting at a Maryland newspaper had damaged the tips of his fingers in an apparent attempt to thwart efforts by police to identify him by his fingerprints, a law enforcement officials tells CBS News. Authorities said the suspect is a white male in his 20s who they have not yet identified.
The suspect was taken into custody at the scene and is not cooperating with investigators, police said. CBS News’ Jeff Pegues reports that the suspect was caught hiding under a desk.
The gunman did not have identification on his person. He’s described as having long hair. A law enforcement source says authorities are using other means of identifying him, including facial recognition technology to search databases of passports and driver’s licenses.
Posted June 28, 2018 by Scared Monkeys Aggrevated Murder, Attempted Murder, Crime, Law Enforcement, Mass Murder, Media, Murder, Newspapers - print media, You Tube - VIDEO | one comment |
Rep. Trey Gowdy (R-SC) Blasts Deputy AG Rosenstein & FBI Director Wray During House Judiciary Committee Hearing … Finish the Investigations ‘The Hell Up Because this Country is Being Torn Apart” (VIDEO)
REP. GOWDY BLASTED ROSENSTEIN AND WRAY ON THE DELAY TACTICS OF DOJ AND THE BIAS OF STRZOK …
This morning during the House Judiciary Committee Hearing with Deputy AG Rosenstein and FBI Director Wray, Rep. Trey Gowdy (R-SC) blasted both of them for their continual delay tactics, stone walling, and lack of producing documents. Gowdy questioned why the so-called “neutral and dispassionate” bias FBI agent Peter Strzok was talking about impeachment within 3 days of Special Counsel Mueller being appointed. That was quicker than the liberal MSM like MSNBC spoke of it.
Gowdy stated to both Rosenstein and Wray, “I realize that neither one of you were there when it happened, but you are both there now. Russia attacked this country. They should be the target. But Russia is not being hurt by this investigation right now, we are. This country is being hurt by it. We are being divided. We have seen the bias. We have seen the bias. We need to see the evidence. If you have evidence of wrong doing by any member of the Trump campaign present it to the damn grand jury. If you have evidence that this President acted inappropriate, present it to the American people. There is an old saying that justice delayed is justice denied. I think right now all of us are being denied. Whatever you got, finish it the hell up because this country is being torn apart.”
Watch Gowdy eviscerate Rosenstein and Wray.
Rep. Trey Gowdy, R-S.C., on Thursday excoriated Deputy Attorney General Rod Rosenstein and FBI Director Christopher Wray instead of asking questions in his first five minutes during the top law enforcement officials’ testimony before the House Judiciary Committee.
“If you have evidence of wrongdoing by any member of the Trump campaign, present it to the damn grand jury,” Gowdy, who is chairman of the House Oversight Committee, said Thursday in reference to special counsel Robert Mueller’s federal Russia investigation.
“If you have evidence that this president acted inappropriately, present it to the American people,” he continued. “There’s an old saying that justice delayed is justice denied. I think right now all of us are being denied. Whatever you got, finish it the hell up because this country is being torn apart.”
Posted June 28, 2018 by Scared Monkeys Department of Justice (DOJ), DOJ - Dept of Justice, FBI, House of Representatives, IG Report, Scandal, Trey Gowdy (SC-R) | no comments |

 RSS
RSS